Key points:
- Healthcare data breaches cost the industry millions of dollars each year.
- For ultimate data security, healthcare organizations should work with companies that prioritize efforts to obtain industry best certification standards – such as HITRUST and SOC 2 compliance.
- HITRUST certifications help organizations maintain a high level of data security, manage risk both internally and externally, and reduce the chances of a data breach.
- SOC 2 is an auditing procedure that ensures your service providers securely manage your data to protect the interests of your organization and the privacy of its clients.
With few exceptions, large healthcare data breaches have been on the rise since 2009. The first three years of the decade have already seen nearly as many large breaches as the last six years of the 2010s, signaling a growing concern for healthcare data security.
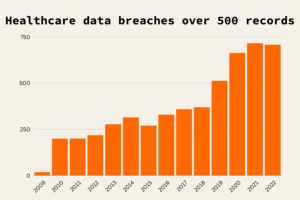
In addition to a tarnished reputation, these cyberattacks and data breaches cost healthcare organizations millions of dollars each year. According to IBM’s 2022 data breach report, the average cost of one healthcare data breach in the United States is $10.1 million – higher than any other industry, and any other nation, for the 12th year. These costs are associated with remediation costs, cyber insurance premium increases, lawsuits, financial penalties, and future investments in security improvement.
Tackling healthcare data security challenges
Healthcare organizations need new data security standards to ensure the safety of their data and their patients. When it comes to providing this support, Q-Centrix feels strongly that a comprehensive data security strategy executed through a continuum of efforts is the only way to fulfill this need. Victor Low, who leads our security efforts as Senior Director, IT, reflects on this commitment,
“Our partner community trusts us with every transaction we make with one of their most valuable assets — their clinical data. We take our responsibility as stewards of this data seriously, and we owe it to them to subscribe ourselves to a higher standard when it comes to security.”
– Victor Low
That dedication reflected in Victor’s words has paid off. For the third year in a row, Q-Centrix is the only healthcare quality data organization to earn the widely coveted recognition of SOC 2 + HITRUST compliance, driving cybersecurity standards for the healthcare industry.
What is SOC 2 compliance?
The SOC 2 – Systems and Organization Controls – audit assesses the strength and application of data security practices. The framework was developed by the American Institute of Certified Public Accountants for the primary purpose of assuring information is stored and processed in a secure way.
The audit assesses a wide range of elements, from our physical hardware infrastructure and use of cloud computing to our team itself and the type of information we manage. SOC 2 compliance standards are based on five Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy.
SOC 2 Trust Services Criteria overview
Security is the basis of SOC 2 compliance and is the driving standard for all Trust Service Criteria outlined below.
Availability – Can data be accessed according to the agreed-upon terms of use and service levels?
The Availability category measures the ability of the data management system to maintain operational uptime and performance to meet business objectives and service level agreements. Performance monitoring, data backups, and disaster recovery plans are examples of the factors considered under this category.
Minimum acceptable performance levels for availability are set by all parties involved and can help mitigate user concerns about downtime. This is especially crucial for hospitals that rely on real-time data to make decisions.
Processing integrity – Does the system deliver the right data at the right place and at the right time?
Removing accidental or unexplained errors is a critical consideration when unlocking the value of clinical data. The processing integrity category assures that our technology processes data in a predictable matter to produce complete, accurate, timely, and reliable information.
Our data integrity program is just one major component of ensuring we meet these stringent requirements to support the critical operational tasks of our partners.
Confidentiality – are data sharing restrictions being met?
Confidentiality is especially important for the sensitive information handled by healthcare organizations. This category requires Q-Centrix to demonstrate the ability to protect this information throughout the entire data lifecycle, from collection and processing to disposal.
Data are considered confidential if access and disclosure are restricted to a specific organization or group of individuals. Other specific requirements are defined by laws and regulations, including HIPAA, internal management, and agreements with our partners. Encryption tools, firewalls, and access controls are all important tools for meeting these criteria.
Privacy – how does the organization collect and use patient information?
Like confidentiality, privacy refers specifically to personally identifiable information, especially critical for healthcare organizations. To meet these criteria, our system’s collection, use, retention, disclosure, and disposal of personal information must meet, at a minimum, the Privacy Management Framework standards set forth by the AICPA. Privacy policies and consent management mechanisms are examples of the tools used.
Going beyond Trust Services Criteria
Beyond the criteria outlined above, Victor points out that approximately 80 new controls, including those focused on ransomware attacks, were added to the audit in 2022 based on evolving security threats and corresponding mitigation practices.
A ransomware attack is typically attempted by a malicious person or group acting as a person, company, or other entity with a seemingly legitimate request. They often send what is called a phishing email to an organization’s employees containing harmful computer code hidden behind a link or in an attachment. Once unleashed, this code seizes and locks the organization’s team out of its own network. The hacker responsible then demands an extravagant ransom to allow the organization to regain access. Making matters worse, the harmful code sometimes infiltrates a network and then sits dormant for months or even years before it becomes active or detectable.
The SOC 2 + HITRUST Security Assessment looks specifically for controls designed to prevent or mitigate this type of threat. An example is the minimum necessary rule — based on the idea that limiting each employee’s network access to only what is necessary to perform their job will reduce the impact of an attack. Another is establishing an ongoing training and test phishing strategy to teach employees how to recognize ransomware phishing attempts and randomly assess their ability to do so.
These examples underscore that an effective privacy and security strategy is not just a one-time effort but rather a deliberate and continuous endeavor involving frequent updates, perpetual assessments, and ongoing learning, with the pinnacle of assessment being the annual audit.
What is HITRUST compliance?
The HITRUST compliance provides requirements for creating, accessing, storing, or exchanging personal health and financial information in a secure and transparent manner. Short for Health Information Trust Alliance, the HITRUST standards are designed to help healthcare organizations manage privacy risks and provide information security. Today, HITRUST has evolved to cover a wide range of security standards, including HIPAA, PCI DSS, ISO, COBIT, and NIST.

Q-Centrix’s approach to data security
Achieving SOC 2 + HITRUST adds to an already-robust and multi-faceted set of data security best practices at Q-Centrix. To support the complex and dynamic environment of healthcare data security, our approach includes six additional factors:
- Complying with the HIPAA and HITECH laws – which establish the provisions for safeguarding personal health information in the United States.
- Following standard data protection best practices – such as encryption for all healthcare data we store and transmit, two-factor login authentication for anyone permitted to access our information systems, and workforce security training.
- Conducting regular system vulnerability scans and penetration testing – to detect weak points in computer networks and equipment and demonstrate how effective security controls are in responding to an attack.
- Adopting the proper physical security elements – including secure entrances, restricted equipment areas, and video camera surveillance.
- Enlisting reputable vendors of our own – especially for cloud storage and communications support (e.g., email, phone system, internal messaging, and other information-sharing systems).
- Having a full security incident response plan in place – with steps to identify, stop, evaluate, and contain a threat or breach, as well as prevent future similar incidents.
Why SOC 2 + HITRUST matter
The most important outcome of the certification is the independent verification it provides. The SOC 2 + HITRUST audit is based on outside principles and was performed by an independent auditor.
“Our current and potential partners now have more than just our word to go on when evaluating us in terms of data security. Plus, maintaining the certification requires an annual review to demonstrate our long-term commitment to compliance.”
– Brian Foy, chief product officer